The Binghamton University connection to Spectre and Meltdown
Research from the Computer Science Department played a role in the recent reveal of a processor design feature that left devices vulnerable to hackers.
Update 04/03/2018: The research team mentioned below recently discovered their own branch prediction processor attack called BranchScope. Read more about the attack here.
It was recently announced that Intel, AMD and ARM processors have a design feature that could allow access to personal information via what are being called Spectre or Meltdown attacks.
The feature, which was originally designed to improve performance, has been a part of processors for over 20 years, but it has taken advances in research to fully understand its potential risk.
Those advances included research from the Binghamton University Computer Science Department.
Exploiting the collisions
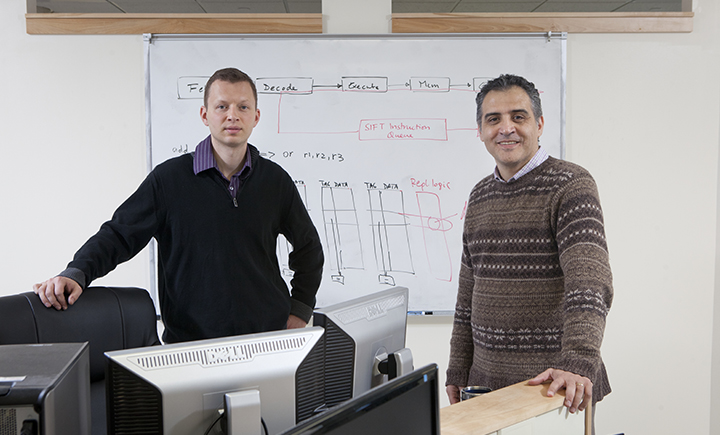
The 2016 study, titled “Jump Over ASLR: Attacking the Branch Predictor to Bypass ASLR,” was a collaboration between computer science professor Dmitry Ponomarev, former Binghamton University computer science professor Nael Abu-Ghazaleh, who now works at the University of California, Riverside, and their former PhD student Dmitry Evtyushkin, who graduated in 2017 and is now an assistant professor at the College of William and Mary.
In their research, Evtyushkin, Ponomarev and Abu-Ghazaleh looked at one way that standard processors could be vulnerable to attacks.
They studied the address space layout randomization (ASLR) which is a process that automatically randomizes the location of information in a device’s memory to protect the machine from a wide range of attacks.
The team identified a way to disable and bypass the ASLR by attacking what is called the branch predictor hardware.
Ponomarev describes the branch predictor as a hardware unit that guides what path a program should take upon encountering a branch instruction, based on the history of previous executions.
“The branch predictor units are shared by various programs and sometimes there can be collisions when two programs access the same branch predictor entry. Then, the information written by one program may impact prediction outcomes of the other,” he says. “These collisions can reduce the predictor accuracy; however, the impact is usually minor so companies allow these collisions to make the design simpler.”
While the collisions are a normal part of the process, the Binghamton team demonstrated in their paper that these collisions can potentially be exploited by a skilled hacker to bypass the ASLR.
Their study was part of a variety of research that started to pull at the common thread of potential security flaws with processors. In fact, the Spectre attacks further built on exploiting these collisions.
The discovery of Spectre and Meltdown
Interestingly, the most recent processor flaw discovery that led to the Spectre and Meltdown attacks was found by multiple researchers within months of each other.
Ponomarev explains, “There had been a lot of research like ours that looked at potential processor issues, so everything was set up for this major development.”
While a variety of researchers had been pointing to a potential risk with processors, Google’s Jann Horn was one of the researchers who discovered the new attacks, which were called Meltdown and Spectre in the academic papers.
In Horn’s extended explanation of the technical aspects of the attacks, he credited the Binghamton University researchers as a source of inspiration.
Horn says their work was “used as a starting point for analyzing the branch prediction of Haswell processors.”
Another researcher who had been looking at the processor flaw was Anders Fogh, a malware analyst for a German firm called GData. In July 2017, he sounded the alarm about a potential way to read kernel memory and cited the research done at Binghamton University as a motivation for his theories.
While Fogh had been unable to develop a final attack to prove his theory, the Meltdown attack followed similar ideas in its working prototype.
In a blog post following the Meltdown and Spectre announcement, Fogh took a look back at what led so many researchers to have the same premonition within the span of a few months.
Fogh again gave credit to Binghamton University’s 2016 research writing, “They didn’t try to read from the kernel but rather found that branch prediction leaked information. This is important because branch prediction is a precursor for speculative execution…”
How to protect your data
When there are reports of a potential wide-reaching security problem, it is understandable that individual users will be nervous about protecting their own data.
Ponomarev says that this is just another attack in the arsenal of the adversaries, and users should follow standard security practices such as applying updates and patches in a timely manner and avoiding visiting suspicious websites or using suspicious apps.
“People should keep their apps and systems updated and make sure they do not allow any malware to run on their devices, but that’s the normal security practice,” explains Ponomarev. “The companies who produce processors are the ones who really need to work on drastic changes to eliminate these types of timing attacks in principle.”
Companies like Intel will need to change the design of their processors to keep users protected.
While attacks like Spectre and Meltdown are difficult for an average hacker to carry out, Ponomarev says that could change in the future. With this new knowledge, an easier attack avenue could be developed later if companies don’t fix their designs.
For Ponomarev, this is just one example of why computer scientists work so hard to understand security vulnerabilities.
“As researchers, we want to find the places that are most susceptible. It helps us stop a problem before it becomes an easy hack and then we can build better and more secure processors,” says Ponomarev. “It would have been impossible to even predict that someone could develop these attacks years ago when the foundations of current hardware architectures were developed.”
According to Ponomarev, “average users should feel safer now that these attacks have been found by reputable researchers instead of malicious hackers.”